Multi-Factor Authentication a Good Solution to Unauthorized Access Problem
The use of only passwords – even well-encrypted ones – for login permission is not enough, it seems, to stem the tide serious problem of black hat hacking and unauthorized access. Across the cybersphere, it seems the more frequently a given company or individual updates their passwords that just as fast there is a “cracker” ready to decrypt them in order to gain unauthorized access. Amidst all of this is the recent statistical revelation that employees are the biggest cyber threat in the workplace. It seems that the only thing agreed-upon in the Admin vs. User game is that passwords alone are not enough to guarantee secure login and access control. They are a distinct problem, in fact, which multi-factor authentication enabling can remedy.
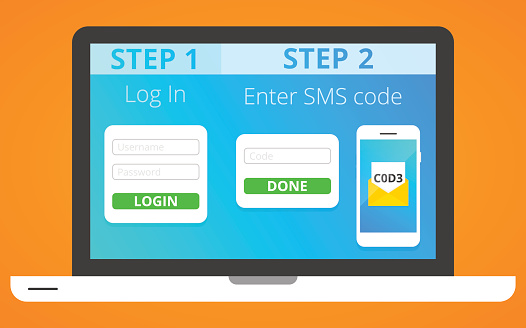
Valid Alternatives
With passwords presenting such a problem globally, the search for valid and viable alternatives is fast becoming essential for any venture. PIN (Personal Identification Numbers) work out to be simply numerical and shorter forms of passwords, though in certain cases PINs can provide greater levels of security, due to being tied to a specific device. Multi-Factor Authentication (AKA MFA, or Two-Factor Authentication, Two-Step Authentication, or TFA), then, presents itself as the best and most valid alternative to passwords in the battle for ultimate security in login access. Why? Because MFA provides a step-by-step, real-time process of validating a user’s identity, the steps for which must happen in a given order if entry is granted. MFA has three essential tiers of authentication, which include:
- Knowledge, in the form of something only the valid user knows, such as a PIN.
- Possession, defined by a thing which only that user possesses such as smartcards, hardware/software tokens, soft tokens, or a registered phone number.
- Inherence, in the form of something only the valid user is, verified through biometric information.
The Case for Multi-Factor Authentication
Multi-Factor Authentication makes the most sense for any business venture or organization that is required to take electronic communication security seriously. Because MFA is tied to users’ identity in a strict way, it largely obviates the most popular form of cyberattacks and threats – leveraging stolen passwords. As a result, MFA provides the highest measure of security assurance for organizations of all types.
And, because MFA can also pinpoint and track user identity in such an exacting manner, enterprises can better track on a use-by-use basis exactly who is accessing their databases, along with when, where, and how. For a long time, SMBs and even corporate structures overlooked the importance of having MFA as part of their IT security, because it was seen as too costly. Now, with the rise of ransomware hacks and other costly cyberthreats, MFA in 2016 is altering the security paradigm through being both easier to implement and use, as well as more affordable.
Many platforms, such as Microsoft, Amazon and Google, now allow you to set up multi-factor authentication for your online accounts. The first factor of which is the traditional username and password (or PIN), while the second is either a phone call that you answer to obtain a verification code, or a phone app notification in which you enter your pre-determined PIN code. Microsoft recently released a new version of their Microsoft Authenticator app for Android and iOS that lets you perform MFA for both your Azure business account and your Microsoft accounts – both personal and business.
Heads in the Cloud
Any technology solution needs to balance sharp-eyed security against the user adoptability quotient. Cloud applications, for one, weren’t designed to work in tandem with legacy MFA capabilities. Those legacy solutions were strictly built for on-premises resources, long before “cloud” or “mobile” meant anything in the world of IT. Recently-generated MFA methods, however, can make strong authentication an easy, convenient, and secure option for virtual and cloud-accessing networks.
Have Questions About Implementing MFA for Your Network?
If you have questions or concerns about multi-factor authentication, {company} is the leader in providing cybersecurity and IT consulting in Fort Lauderdale. Contact one of our expert IT staff at {phone} or send us an email at {email}, and we will be happy to help you attain better security verification methods for your business network.





