ECW: Blog
Lightning Fast Guide to Using Slide Master in PowerPoint 2016
Do you find yourself making a lot of formatting changes to your slideshows? Do you have to constantly rearrange the placeholders in each slide so things look the way you feel they should? Do the color options never seem to…
Read MoreIs Human Error the Leading Cause of Data Breaches in the U.S.?
New Study Shows That the Global Cost of a Data Breach Is Up in 2018 The Ponemon Institute recently released its annual Cost of Data Breach Independent Study that was sponsored by IBM Security. This study included two new factors…
Read MoreHow Do I Find the Right IT Managed Services Provider?
Identifying the Right IT Services Provider for Your Business IT service providers, also called managed services providers (MSPs), are in the business of managing a company’s IT needs. IT service providers can offer their services both remotely and on-site. They…
Read MoreCan The Cloud Simplify Your IT Security And Compliance? (Questions & Answers)
Compliance and IT security can be complex. Can the cloud really take some of the burdens off your shoulders? In this article, we’ll examine the facts and get you the answers you need to make an informed decision about putting your data, applications, and virtualized machines into the cloud.
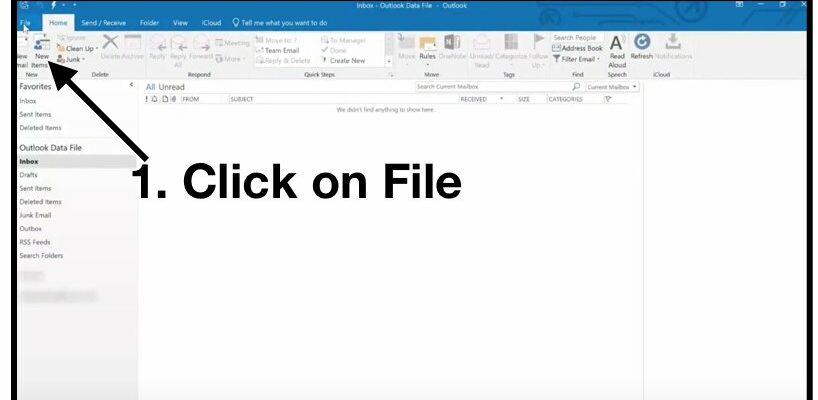
Read MoreDo You Know How to Add Email Signatures?
Step-by-Step Instructions on How to Add your Email Signature in Outlook, Outlook.com, and Gmail [youtube https://www.youtube.com/watch?v=n9ubHsx-eRo]Creating a signature that will leave a lasting impression at the end of an email is essential in today’s business world. However, users often struggle…
Read MoreGirls in Tech: Girl Scouts of the USA Adds New Badges
Girl Scouts of the USA recently announced the addition of 30 new badges now available for Girl Scouts aged 5-18. The new badges were created to address a number of today’s most important social issues, including environmental advocacy, cybersecurity, robotics,…
Read MoreIntel Chip Vulnerabilities: What We Know So Far!
What Do We Know About Terminal Fault (L1TF) Chip Vulnerabilities? Understanding The L1 Terminal Fault (L1TF) Intel has recently confirmed L1 Terminal Fault (L1TF) chip vulnerabilities in its processors that can be manipulated by malware and malevolent virtual machines with…
Read MoreWhy Should My Company Upgrade to Windows 10?
If you are in a startup company or run a small business, the simplest software update can easily cause anxiety for you and your group of employees. Everyone has experienced the update that causes glitches and hiccups that can disrupt…
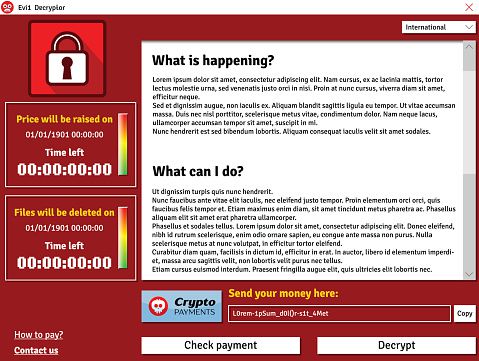
Read MoreAugust 2018 Ransomware Update
The Newest Forms Of Ransomware & How To Protect Your Business From Them The Situation Ransomware is now one of the top security concerns for businesses and organizations of all sizes. The City of Atlanta was hit with a ransomware…
Read MoreCheck Out The 10 Best Tablets of 2018 (Ratings/Reviews)
They are the next best thing to hauling your laptop around to school and on flights, and they’ve become the weapon of choice for parents with fussy toddlers in public spaces. But while tablets have earned their accolades in recent…
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (561) 303-2310 or complete the form below and we'll help in any way we can.
"*" indicates required fields