ECW: Blog
Raising Awareness of Digital Risks
Raising Awareness of Digital Risks: What Businesses Need to Know Key Points: Rapid technological advancement has led to new risks that businesses must now face. There are many steps businesses can take to mitigate these risks, but they need to…
Read MoreBusiness Continuity Planning: Developing An Impact Analysis
According to FEMA, 40% of businesses hit with a disaster never recover, and this rate more than doubles for those without a business continuity plan. While the two are linked, a business continuity plan shouldn’t be confused with disaster recovery. You…
Read MoreInvest in Valuable Technology for Quality Profitable Work by Your Sales Team
Sales Technology Improves Results and Leads to Better Processes Learn how sales tools that use some of the latest technologies, including automation, machine learning and artificial intelligence, deliver better outcomes. To remain competitive today, your salespeople need all the advantages…
Read MoreIntuitive Scheduling: The Missing Link for a Happy Office
Finding the right scheduling software can make everyone happier, and thereby make everything run a bit easier and a bit more smoothly. Here is what you need to find in the optimal scheduling software program, and where to find it.…
Read MoreHow to Protect Your Business from SHTML Phishing
Protecting Your Data from SHTML Phishing Data security is vital to any business. Learn how SHTML phishing works and how to minimize the risk of your data falling into the hands of attackers. Email phishing has been in the playbook…
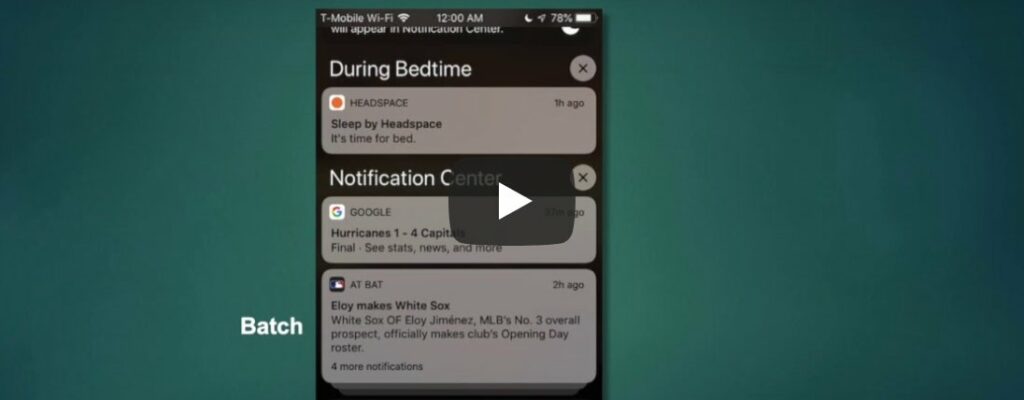
Read MoreEfficiently Manage Notifications In iOS 12
Apple’s mobile iOS operation system is one of the most popular platforms in the world. With more than 1.3 billion devices running iOS worldwide, Apple has clearly done an excellent job of providing a world-class experience for its users. Watch the video…
Read MoreTop Ways to Avoid Phishing Scams (Including Spear Phishing)
Phishing scams — and, increasingly, spear-phishing scams — are the number one way that cyber hackers gain access to closed computer systems, steal information and money, and corrupt data. Let’s take a look at what phishing and spear-phishing scams really…
Read MoreHow Are Face and Touch Recognition Changing iCloud Access?
How Are Face and Touch Recognition Changing iCloud Access? Apple may be testing new security procedures for iCloud.com with its next OS release. 9to5mac has reported that the beta for iPadOS 13, iOS 13, and macOS Catalina can use Touch…
Read MoreHow Does Windows 10 Improve Security and Data Protection?
Windows 10 comes a step closer to preventing cyberattacks and privacy threats facing users. It’s a next-generation solution that helps you fight threats from hackers and criminals who target your business. This is a big plus for cybersecurity managers. The…
Read MoreHow Is Patient Scheduling IT Increasing Patient Happiness?
Patient scheduling IT doubles the output of booking agents and cuts the time needed to schedule an appointment in half. This can increase the happiness of patients and physicians by lowering the costs of healthcare. When health care professionals digitize…
Read MoreRecent Posts
How can we help?
Whether you need immediate help with an IT issue or want to discuss your long-term IT strategy, our team is here to help.
Call us at (561) 303-2310 or complete the form below and we'll help in any way we can.
"*" indicates required fields